Regarding cyber security, zero trust focuses on device and network, data access type, session activity, and time of day. Zero trust models help organizations contain the damage. Read more about zero trust in cyber security.
Table of Contents
Don’t trust anyone
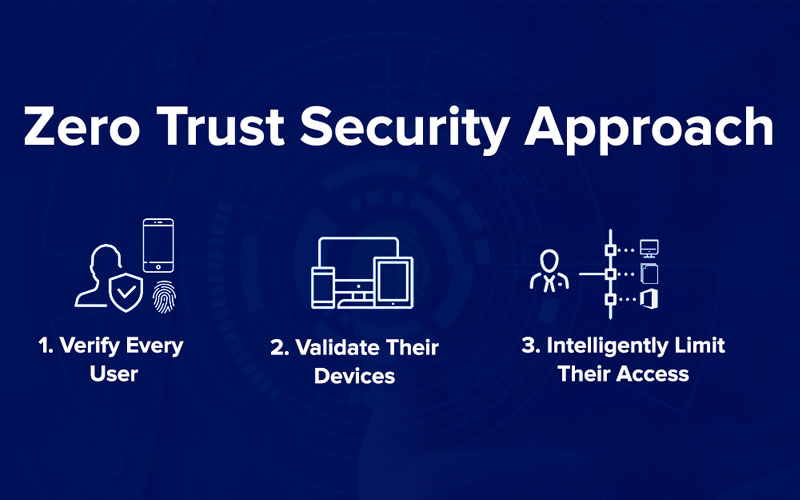
If you are wondering what is a zero trust security network, read this article. “Zero trust” refers to a system of authentication, authorization, and monitoring that requires constant verification of any user or system. This cybersecurity model is growing in popularity and aims to keep pace with bad actors and breaches, especially given recent events.
The “zero trust” concept has many benefits. First, it can improve security operations. Organizations should deploy various subprojects rather than relying on a single vendor, such as identity management, single sign-on, and zero-trust infrastructure. Organizations can improve their cyber defenses by focusing on these technologies.
Micro-segmentation
A fundamental aspect of micro-segmentation in cyber security is that it isolates network elements from each other. This approach is a significant step from the traditional security perimeter model because it allows network administrators to separate each element inside a perimeter from the rest. As a result, micro-segmentation can isolate individual applications, workloads, and operating systems within a network and effectively prevents privilege escalation and lateral movement.
Despite its potential benefits, micro-segmentation has some challenges. Implementing it requires a deep understanding of the network security environment. Legacy architectures evolve piecemeal over time, and little documentation is available to help administrators apply micro-segmentation to their networks. Creating micro-segmented policies may create ambiguity and disagreements over a specific application or process.
Continuous monitoring
Zero trust in cyber security means continuous monitoring. In a Zero Trust model, privileged user activity must be monitored and documented to determine whether an attack has been successful. To accomplish this, security controls must be well integrated into the environment to monitor and respond to threats. This can be achieved by integrating security platforms, which can automate risk-response workflows and enable automated risk detection and response. To determine whether a security control meets the requirements of the Zero Trust model, it is essential to perform a thorough risk assessment of its features.
Currently, zero trust focuses on user access, role-based access, lateral movement, and microperimetry. It neglects the hygiene process, vulnerability management, and patch management. Zero trust is not suitable for organizations with remote access or privileged users. Managing user access to resources is pointless if some risks and vulnerabilities exist. This way, continuous monitoring, and privileged access management will be crucial in addressing zero-trust security.
Integration with existing security controls
Integrating new and existing security controls into one single platform is an essential step toward achieving the ultimate security goal – reducing risk, preventing incidents, and reacting quickly when incidents occur. While commerce has well-defined mechanisms for achieving these goals, security is a more complex domain. Security failures are typically associated with a lack of integration, and sophisticated attackers routinely circumvent existing controls. Therefore, it is imperative to consider the advantages of integrated security controls and how they can be implemented into a comprehensive security strategy.
Cybersecurity has become more critical than ever, and organizations are putting more emphasis on data integration. Unfortunately, today’s large-scale integration projects often involve a variety of data silos containing mission-critical information. One study revealed that organizations that focus only on perimeter protection and tactical details are exposing themselves to enormous cyber risks. Not only does this approach lead to data loss, but it also exacerbates governance issues.
Developing a zero-trust environment
Developing a zero-trust environment in cybersecurity means not relying on “inside the perimeter” security. Instead, it focuses on policy, identity, posture, and granular control of communications, instead of trust. This approach is not without its challenges, however. For example, zero trust tools require redundant technologies to support different environments. They also may be unable to place controls close to the user or application. In addition, many legacy systems and third-party applications have been designed around implicit trust, and administrators must create a new framework and infrastructure to support zero trust models. This process adds complexity and requires buy-in from all levels of the organization.
First, Zero Trust solutions require ongoing maintenance. Like any successful security or IT protocol, Zero Trust requires ongoing work. Likewise, to be successful, micro-segmentation requires continuing care and configuration. As IP data changes, teams must constantly update and configure them to ensure zero-trust. Unless this is done regularly, micro-segmentation can interrupt services and work. As a result, it can be a costly and time-consuming task.